Do you ever wonder how famous and successful public figures such as Bill Gates and Kim Kardashian were scammed and lost up to $100,000? Phishing scams have been a ground-breaker for everyone with a social media account or phone number. Today you will learn how to how can you protect yourself from phishing, identify and avoid phishing scams in 2024, so you can be safer online.
Phishing scams have been a significant threat in 2024. Hackers can use multiple methods to quickly and easily access your account, fool you into a fake setting, and get what they are looking for without you realizing it.
First this article will explain phishing scams, how they are perpetrated, how can you protect yourself from phishing and how to identify them to reduce phishing scams and ensure the safety of every individual and organization alike. We recently discussed QR Code Scams, part of the same Scam Family.

What are phishing scams?
Phishing is a scamming tactic that targets people by asking them for sensitive information through various tactics. This information can include credit card details, banking details, passwords, and more.
The primary and most common ways a phishing scam is perpetrated are through emails and text messages. However, other methods are also used, such as websites and phone calls. A phishing scam message will be too good to be true, such as claiming that you have won something or that a huge deal is available for a limited amount of time. Item delivery messages are now the most common, asking you for details, which will give the phishers access to your bank records.
You must be able to catch phishing scams at the first glance. How you can protect yourself from phishing in 2024 will be easier if you know the different kinds of phishing scams. Some of the common types are listed below:
Email Phishing
Email phishing is still the most common type of phishing attack. A long and lucrative email will be sent to the target audience in bulk, appearing from an authentic and legitimate business or organization. These emails include the sender’s logo, a false domain name that matches a higher-class business, and masking other information.
The message usually has an overall format of strong, built-up emotions, such as fear, greed, or urgency to accept. A typical message will consist of connecting things along the lines of “Please update your user profile,” “Your closing documents are ready,” or “Problem with your order.”
The body of the message urges the reader to update their profile or confirm a package delivery by clicking on a fake hyperlink. This leads them to type in their authentic login credentials, and this is how hackers can steal information.
Spear Phishing
Spear phishing attacks target an individual, usually someone who has privileges such as access to sensitive data, special authority, or networking resources. Before sending a message, the hacker will study the targeted individual to gain information so that they can act out as their trusted fellows. These could be a friend, a co-worker, a boss, or any other relative. This is a very dangerous attack and one that is important to know how can you protect yourself from spear phishing.
Hackers gain information through social media connections, especially when one congratulates another on an achievement.
When they gain the information they need, the spear phisher sends a message containing personal or financial information to the target. For example, “I know you are going to be flying tonight to XY city. Can you please pay this invoice before you leave or transfer it to X to this account?”
The primary target audience for this type of phishing is wealthy individuals who can quickly and readily send an amount to an account.
SMS Phishing or Smishing
These type of phishing attacks are done through a text message. It is the most effective attack out of the rest. The message will be relevant to a smartphone account or app. Difficult phishing scam to protect yourself from if not educated. The target will receive a message offering a gift as a thanks or appreciation for paying a bill or asking them to update their credit card information. The message will contain high quality images and the fake websites are of high quality
Voice Phishing Or Social Engineering (Vhishing)
Voice phishing is done through phone calls. The hackers use a voice-over to scam millions of targeted audiences. They use a caller ID to make their phone calls, as this helps to make the call look more legitimate.
The main message of voice phishing is to scare the individual into thinking they have overdue payments to the IRS, or are facing credit card problems. Those who respond to the phone calls will get scammed, as private information will be asked.
New for 2025 is a warning that callers will also try to get you to urge you to part with your information, claiming to be a helpdesk or other IT professional. Trying to tell you your computing device is infected and this needs to be addressed now. Often the sign up for this will ask for your personal information, Google forms are often used by these cybercriminals as it it very easy to direct the information to a database they will use. Once they have gained remote access to your computing device (whatever type that may be) it is over and you have been scammed.
Clone Phishing
Clone phishing is a newer form of email phishing. In this type of phishing, hackers create a cloned email of a real email message with attachments and send it to the target. The attachments are replaced with malware that allows the hackers to access all your sensitive information. However, the email looks like original and authentic documents.
Identifying Phishing Scams – Top Tips and Tricks
There are different ways you can identify phishing scams. It is important to recognize phishing scams so that you are safe from the harm that they can cause. Our Top tips based on our own experience include:
| Key Indicator | Description |
|---|---|
| Bad Communication | If the language of the message is threatening or unusual, it is most likely to be a scam message. Professional emails from authentic companies will have good grammar and spelling. |
| Unknown Links and Suspicions | If you spot any links that do not concern the message, it is most likely to be malware that steals your sensitive information. Mouse Hover over the links If they do not relate to the content of the message. The are fake. |
| Requests for Personal Information | A message that directly or unusually asks for your personal information will always be a scam. Ensure you keep your sensitive information private. |
| Mimicking Other Legitimate Businesses | Look for any images or brand logos. If they are blurry, low-quality, or have bad graphics, it is a scam. Check for mismatched business logos and names as well. |
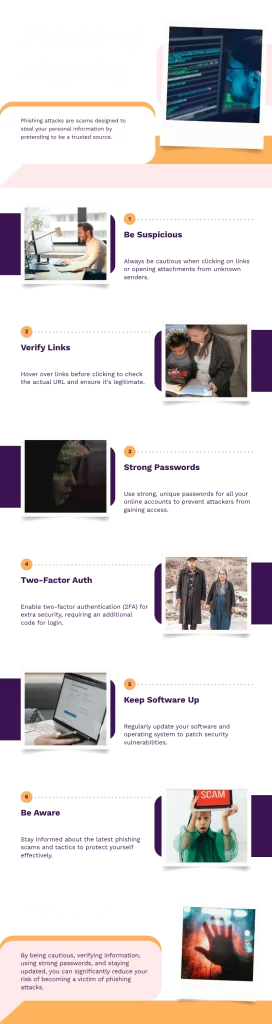
How Can You Protect Yourself From Phishing – Key Points
Avoiding phishing scams will ensure that you never fall into the dreadful tricks hackers play. Some ways how you can do this are by:
Educating oneself and others
Knowing the types of phishing and how they play around a target is necessary to leave a fake message behind. Always stay up-to-date with modern tricks and share the information with others as well. The US Government also has important data on this threat.
Create a defense
There are multiple ways you can get rid of scam emails and messages without them even reaching you. Set email filters and other spam detectors on your computers, laptops, and mobile phones through different apps and websites. You can also install reliable security software that helps you eliminate scam messages.
Safe and secure browsing
Ensure that you have a safe and secure browsing network. Verify the URLs before giving your personal information to the website. Once you have confirmed the authenticity of the URL, you can bookmark it to remain confident in it.

Do not overshare
Whenever you are providing information, do not do it with ease or in one go. Always confirm and get the trust that is needed. Moreover, make sure you do not share your personal information through messages or emails. You can use two-factor authentication for extra security.
Report Scams
If you are caught in a phishing scam or anyone else, ensure that you report it to your relatives and email provider so that they are aware.
Scam protection- steps to take
If you are a victim of a phishing scam then be sure to take these phishing scam protection steps.
Steps to Follow After a Scam
| Step | Action |
|---|---|
| Step 1 | Quick Action: Immediately disconnect your device from the internet and reset all passwords. |
| Step 2 | Report: Notify your bank/financial institution and local cybercrime units. |
| Step 3 | Monitor: Watch for unusual activity and inform your bank again if needed. |
| Step 4 | Call an Expert: Contact a cybersecurity expert and follow their recommendations. |
Conclusion
Consider all of the ways you can protect yourself from phishing in 2024. Being aware of modern technology and the different types of phishing scams will help you identify messages with ease. Moreover, install secure security apps and email filtering actions to filter out scam emails.
Always get the right help whenever you are stuck in a situation as such and inform other relatives as well so that they are safe. Being aware of scams in the modern day is a crucial element. While having all the information about scams and how they are done, you will be safe from all kinds of phishing scams.
FAQ
What scams are going around right now?
Email and SMS phishing scams are the most common types of scams.
Which phishing clues can you identify?
You can identify a phishing scam by looking at the tone of the message, the fake business name or logo, asking for personal information, unusual links, and attachments.
What will a scammer ask you to do in a phishing attack?
A scammer will ask you to provide them with personal information such as credit card information, and bank details. They can ask this in multiple ways such as telling you there is a problem with your purchase or disguising it as a relative and asking for a specific amount.
What are the most common targets of phishing scams?
The most common targets are those who are wealthy or have multiple accounts online on different platforms.


thanks for info.